In vista dei prossimi corsi MISP che si terranno a Roma, in AgID e Banca D’Italia fra la fine di Maggio e l’inizio di Giugno, mi è sembrato utile condividere alcuni appunti sparsi sulla piattaforma e di farlo prevalentemente in Italiano. In questa prima puntata sarà riportata la procedura di installazione di MISP in ambiente Ubuntu 16.04 LTS. Si tratta di una riproposizione quasi fedele della guida pubblicata dagli stessi sviluppatori di MISP, con qualche piccola personalizzazione dettata più dal vezzo personale che da altro.
In vista dei prossimi corsi MISP che si terranno a Roma, in AgID e Banca D’Italia fra la fine di Maggio e l’inizio di Giugno, mi è sembrato utile condividere alcuni appunti sparsi sulla piattaforma e di farlo prevalentemente in Italiano. In questa prima puntata sarà riportata la procedura di installazione di MISP in ambiente Ubuntu 16.04 LTS. Si tratta di una riproposizione quasi fedele della guida pubblicata dagli stessi sviluppatori di MISP, con qualche piccola personalizzazione dettata più dal vezzo personale che da altro.
1 Aggiornamento sistema
Una volta installato il sistema base Ubuntu 16.04 LTS Server effettuare un aggiornamento di sistema, per assicurarsi di aver installato le ultime patch di sicurezza ed aggiornamenti software generici.
:~$ sudo apt-get update --fix-missing :~$ sudo apt-get upgrade
2 Installazione Postfix
Si procede all’installazione di postfix.
:~$ sudo apt-get install postfix
Lo si configuri come “Sistema satellite“.
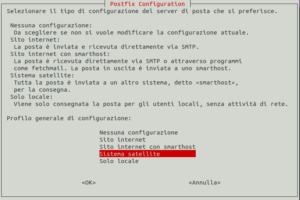
Questa guida non si occupa della configurazione di postfix. Al momento si configurerà “example.com” come relayhost del mail server. Sarà cura dell’utente terminare la corretta configurazione di postfix, in funzione delle proprie esigenze e vincoli.
:~$ sudo postconf -e 'relayhost = example.com' :~$ sudo postfix reload
3 Installazione pacchetti e librerie necessarie
Di seguito si installeranno i vari pacchetti, interpreti, librerie necessarie al corretto funzionamento di MISP, che per garantire le prestazioni di sharing multipiattaforma che si prefigge, ha necessità di un certo numero e di una certa qualità di applicativi da utilizzare.
:~$ sudo apt-get install curl gcc git gnupg-agent make python python3 openssl redis-server sudo vim zip
4 Installazione MariaDB
Sarà ora necessario installare MariaDB, un fork del più famoso MySQL, utilizzato dagli stessi sviluppatori di MISP.
:~$ sudo apt-get install mariadb-client mariadb-server :~$ sudo mysql_secure_installation
Non ci si scordi mai di mettere in sicurezza l’installazione del database server.
5 Installazione e prima configurazione di Apache
Si eseguano i comandi di seguito riportati.
:~$ sudo apt-get install apache2 apache2-utils :~$ sudo a2enmod ssl :~$ sudo a2enmod rewrite :~$ sudo a2enmod headers :~$ sudo a2dissite 000-default :~$ sudo a2ensite default-ssl :~$ sudo service apache2 restart
Nei fatti, oltre all’installazione del webserver si abilitano i moduli ssl, rewrite e headers. Dopo di che si disabilita il virtualhost 000-default per attivare il default-ssl. Anche se questo verrà disattivato in un successivo passaggio, tenerlo attivo ci consente di testare il corretto funzionamento del webserver sotto SSL.
6 Installazione PHP e librerie necessarie
:~$ sudo apt-get install libapache2-mod-php php php-cli php-crypt-gpg php-dev php-json php-mysql php-opcache php-readline php-redis php-xml :~$ sudo service apache2 restart
7 Codice MISP
Adesso è possibile procedere all’installazione di MISP da codice sorgente. Questi verranno gestiti direttamente tramite Git e la piattaforma GitHub. È possibile anche scaricare manualmente i sorgenti e procedere ad installazione manuale. Ma in questo caso il processo di aggiornamento del software richiederebbe molto più effort, dovendo di volta in volta aggiornare manualmente la piattaforma. Utilizzando Git in questa fase dell’installazione ci si assicura il mantenimento di MISP a medio/lungo termine a costi relativamente bassi.
Si crei una nuova cartella in /var/www che ospiterà la piattaforma MISP
:~$ sudo mkdir /var/www/MISP
Si assegni la nuova directory all’utenza di default del webserver, che negli ambienti Debian/Ubuntu è www-data
:~$ sudo chown www-data:www-data /var/www/MISP
A questo punto possiamo scaricare i sorgenti di MISP, utilizzando git come gestore di versione.
:~$ sudo -u www-data git clone https://github.com/MISP/MISP.git /var/www/MISP Cloning into '/var/www/MISP'... remote: Counting objects: 56839, done. remote: Compressing objects: 100% (149/149), done. remote: Total 56839 (delta 234), reused 304 (delta 210), pack-reused 56480 Ricezione degli oggetti: 100% (56839/56839), 43.75 MiB | 3.25 MiB/s, done. Risoluzione dei delta: 100% (42306/42306), done. Checking connectivity... fatto.
Effettuare il checkout della versione all’ultima disponibile.
:~$ sudo -u www-data git checkout tags/$(git describe --tags `git rev-list --tags --max-count=1`) Note: checking out 'tags/v2.4.91'. You are in 'detached HEAD' state. You can look around, make experimental changes and commit them, and you can discard any commits you make in this state without impacting any branches by performing another checkout. If you want to create a new branch to retain commits you create, you may do so (now or later) by using -b with the checkout command again. Example: git checkout -b <new-branch-name> HEAD si trova ora a 4ad7a4a... Merge branch '2.4' of github.com:MISP/MISP into 2.4
Alla data del presente articolo, la versione di checkout disponibile è la 2.4.91. Se si desidera effettuare un ulteriore controllo, è possibile visitare la home page del repository MISP su GitHub.
Infire configureremo git per ignorare le differenze fra permessi di file locali e remoti.
:~$ sudo -u www-data git config core.filemode false
8 Installare STIX
MISP è STIX compliance per molti aspetti relativi alla gestione degli IoC. Gestisce sia il formato STIX 1.x che il formato 2.x, ma necessita delle librerie ufficiali. Di seguito si procederà ad installarle ad uso e consumo dell’applicativo.
:~$ sudo apt-get install python-dev python-pip python3-pip libxml2-dev libxslt1-dev zlib1g-dev python-setuptools :~$ cd /var/www/MISP/app/files/scripts :~$ sudo -u www-data git clone https://github.com/CybOXProject/python-cybox.git :~$ sudo -u www-data git clone https://github.com/STIXProject/python-stix.git :~$ cd /var/www/MISP/app/files/scripts/python-cybox: :~$ sudo python setup.py install :~$ cd /var/www/MISP/app/files/scripts/python-stix :~$ sudo python setup.py install
Installare mixbox in quanto nuova dipendenza per STIX.
:~$ cd /var/www/MISP/app/files/scripts/ :~$ sudo -u www-data git clone https://github.com/CybOXProject/mixbox.git :~$ cd /var/www/MISP/app/files/scripts/mixbox :~$ sudo python setup.py install
Infine, installare STIX2 (richiesto python3)
:~$ pip3 install stix2
9 Installare CakePHP
CakePHP è il framework di sviluppo su cui si basa gran parte dell’applicativo. Oltre a gestire l’interfaccia utente, CakePHP è in grado di gestire i job del server, fondamentali per la sincronizzazione fra diverse istanze MISP. Di seguito si procederà dando per scontato che si utilizzeranno tutte le configurazioni proposte dal team ufficiale di MISP.
:~$ cd /var/www/MISP :~$ sudo -u www-data git submodule init :~$ sudo -u www-data git submodule update :~$ sudo -u www-data git submodule foreach git config core.filemode false
I pacchetti di seguito installati via composer del PHP sono necessari proprio per la funzionalità di gestione job e code, deputata al framework CakePHP.
:~$ cd /var/www/MISP/app :~$ sudo -u www-data php composer.phar require kamisama/cake-resque:4.1.2 :~$ sudo -u www-data php composer.phar config vendor-dir Vendor :~$ sudo -u www-data php composer.phar install
Abilitare CakeResque con PHP-Redis
:~$ sudo phpenmod redis
Infine copiare il relativo file di configurazione nella directory applicativa di seguito riportata.
:~$ sudo -u www-data cp -fa /var/www/MISP/INSTALL/setup/config.php /var/www/MISP/app/Plugin/CakeResque/Config/config.php
Infine, settare correttamente i permessi delle directory di lavoro.
:~$ sudo chown -R www-data:www-data /var/www/MISP :~$ sudo chmod -R 750 /var/www/MISP :~$ sudo chmod -R g+ws /var/www/MISP/app/tmp :~$ sudo chmod -R g+ws /var/www/MISP/app/files :~$ sudo chmod -R g+ws /var/www/MISP/app/files/scripts/tmp
10 Creazione e configurazione database
A questo punto ci occuperemo di configurare il database e prepararlo per poter ospitare gli eventi MISP. Per questa fase servirà l’utilizzo della password di root del database sql creata al precedente punto 4.
:~$ sudo mysql -u root -p MariaDB [(none)]> create database misp; MariaDB [(none)]> grant usage on *.* to misp@localhost identified by 'password'; MariaDB [(none)]> grant all privileges on misp.* to misp@localhost; MariaDB [(none)]> flush privileges; MariaDB [(none)]> \q
È stato creato il database “misp” a cui ha accesso l’utente “misp” a cui è stata assegnata la password “password” (per ambienti di produzione sarà richiesta una certa complessità della password).
Sarà ora possibile importare una schema database vuoto.
:~$ sudo -u www-data sh -c "mysql -u misp -p misp < /var/www/MISP/INSTALL/MYSQL.sql"
11 Configurazione webserver Apache2
Per la configurazione del webserver Apache, si userà il FQDN “misp.local”. Come prima cosa si dovrà controllare la versione del webserver installata.
:~$ sudo apache2 -v Server version: Apache/2.4.18 (Ubuntu)
Qualora non si abbia altra disponibilità, sarà necessario generare un certificato SSL self signed. Procedere come di seguito specificato.
:~$ sudo openssl req -newkey rsa:4096 -days 365 -nodes -x509 -keyout /etc/ssl/private/misp.local.key -out /etc/ssl/private/misp.local.crt Generating a 4096 bit RSA private key ........................++ .......................++ writing new private key to '/etc/ssl/private/misp.local.key' ----- You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. ----- Country Name (2 letter code) [AU]:IT State or Province Name (full name) [Some-State]:Italy Locality Name (eg, city) []:Rome Organization Name (eg, company) [Internet Widgits Pty Ltd]:MyCompany Organizational Unit Name (eg, section) []:SecUnit Common Name (e.g. server FQDN or YOUR name) []:misp.local Email Address []:misp@misp.local
Creare e modificare un nuovo file di configurazione VirtualHost di Apache2.
:~$ sudo nano /etc/apache2/sites-available/misp-ssl.conf
Come configurazione del VirtualHost si propone la seguente.
<VirtualHost *:80>
ServerName misp.local
Redirect permanent / https://misp.local
LogLevel warn
ErrorLog /var/log/apache2/misp.local_error.log
CustomLog /var/log/apache2/misp.local_access.log combined
ServerSignature Off
</VirtualHost>
<VirtualHost *:443>
ServerAdmin misp@misp.local
ServerName misp.local
DocumentRoot /var/www/MISP/app/webroot
<Directory /var/www/MISP/app/webroot>
Options -Indexes
AllowOverride all
Require all granted
</Directory>
SSLEngine On
SSLCertificateFile /etc/ssl/private/misp.local.crt
SSLCertificateKeyFile /etc/ssl/private/misp.local.key
LogLevel warn
ErrorLog /var/log/apache2/misp.local_error.log
CustomLog /var/log/apache2/misp.local_access.log combined
ServerSignature Off
Header set X-Content-Type-Options nosniff
Header set X-Frame-Options DENY
</VirtualHost>
Disabilitare il VHost defailt-ssl.conf ed abilitare il nuovo dedicato a MISP.
:~$ sudo a2dissite default-ssl :~$ sudo a2ensite misp-ssl :~$ sudo service apache2 restart
Se lo si ritiene necessario, è anche possibile utilizzare una configurazione di log rotation disponibile nelle directory di installo di MISP.
:~$ sudo cp /var/www/MISP/INSTALL/misp.logrotate /etc/logrotate.d/misp
12 Configurazione applicativa di MISP
Questa fase risulta molto delicata. Seppur qualsiasi errore è in qualche modo rimediabile, quanto configurato qui avrà impatto sull’utilizzo stesso della piattaforma e modifiche a posteriori potrebbero risultare in una pardita di informazioni, anche se mai possono risultare in una perdita di dati. Quanto stabilito in questa fase, seppur di stampo prettamente sistemistico avrà impatto operativo notevole. Si consiglia di approfondire questa fase attingendo ad informazioni dettagliate disponibili nel sito del CIRCL.LU.
Effettuare la copia dei seguenti file.
:~$ sudo -u www-data cp -a /var/www/MISP/app/Config/bootstrap.default.php /var/www/MISP/app/Config/bootstrap.php :~$ sudo -u www-data cp -a /var/www/MISP/app/Config/database.default.php /var/www/MISP/app/Config/database.php :~$ sudo -u www-data cp -a /var/www/MISP/app/Config/core.default.php /var/www/MISP/app/Config/core.php :~$ sudo -u www-data cp -a /var/www/MISP/app/Config/config.default.php /var/www/MISP/app/Config/config.php
Nel file “database.php” andrà configurato l’utente MariaDB creato nei punti precedenti.
:~$ sudo -u www-data nano /var/www/MISP/app/Config/database.php
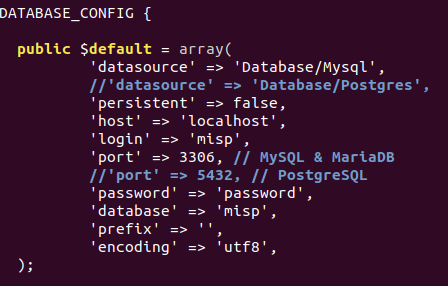
Nel file “config.php” è necessario modificare il SALT di base dell’applicazione (che deve essere di 32 byte) ed altre opzioni, come il “baseurl” che descrive la URL di base dell’applicativo, l’opzione “org” con cui è possibile settare il nome dell’organizzazione di default e altro. Moltre di queste opzioni potranno poi essere gestite da pannello di controllo.
:~$ sudo -u www-data nano /var/www/MISP/app/Config/config.php
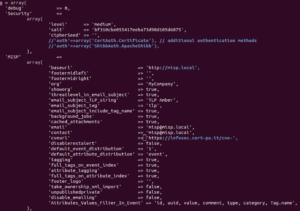
Infine si settano i permessi dei file correttamente.
:~$ sudo chown -R www-data:www-data /var/www/MISP/app/Config :~$ sudo chmod -R 750 /var/www/MISP/app/Config
13 Chiave di cifratura GPG
Per consentire all’applicativo l’invio di email cifrate è necessario creare una coppia di chiavi GPG, avendo cura di generare la chiave per lo stesso indirizzo email configurato nel file “config.php”.
:~$ sudo -u www-data gpg --homedir /var/www/MISP/.gnupg --gen-key gpg (GnuPG) 1.4.20; Copyright (C) 2015 Free Software Foundation, Inc. This is free software: you are free to change and redistribute it. There is NO WARRANTY, to the extent permitted by law. gpg: portachiavi "/var/www/MISP/.gnupg/secring.gpg" creato gpg: portachiavi "/var/www/MISP/.gnupg/pubring.gpg" creato Selezionare il tipo di chiave: (1) RSA e RSA (predefinito) (2) DSA ed Elgaman (3) DSA (solo firma) (4) RSA (solo firma) Selezione? 1 La lunghezza delle chiavi RSA è compresa tra 1024 e 4096 bit. Quale dimensione impostare per la chiave? (2048) 4096 La dimensione chiave richiesta è 4096 bit Specificare la durata di validità della chiave. 0 = la chiave non scade <N> = la chiave scade dopo N giorni <N>w = la chiave scade dopo N settimane <N>m = la chiave scade dopo N mesi <N>y = la chiave scade dopo N anni Per quanto tempo deve essere valida la chiave? (0) 365 La chiave scade il mar 21 mag 2019 11:16:20 CEST È tutto corretto? (s/N) s È necessario un ID utente per identificare la propria chiave; il software costruisce l'ID utente a partire da nome reale, commento e indirizzo email in questa forma: "Mario Rossi (commento) mario.rossi@example.net" Nome reale: Misp Local Indirizzo email: misp@misp.local Commento: È stato selezionato questo USER-ID: "Misp Local <misp@misp.local>" Modificare (n)ome, (c)ommento, (e)mail oppure (o)k/(u)scire? o È necessaria una passphrase per proteggere la proprio chiave segreta. Passphrase: gpg: /var/www/MISP/.gnupg/trustdb.gpg: creato il trustdb gpg: chiave 24C4188D contrassegnata come completamente affidabile chiavi pubbliche e segrete create e firmate. gpg: controllo del trustdb gpg: necessari: 3 marginali, 1 completi, modello di fiducia PGP gpg: livello: 0 valido: 1 firmato: 0 fiducia: 0-, 0q, 0n, 0m, 0f, 1u gpg: il prossimo controllo del trustdb sarà eseguito il 2019-05-21 pub 4096R/24C4188D 2018-05-21 [scadenza: 2019-05-21] Impronta digitale della chiave = 0C94 3FD0 4E3C F36D C33C 0B03 82B1 3167 24C4 188D uid Misp Local <misp@misp.local> sub 4096R/C9565802 2018-05-21 [scadenza: 2019-05-21]
Esportare la chiave pubblica nella webroot.
:~$ sudo -u www-data sh -c "gpg --homedir /var/www/MISP/.gnupg --export --armor misp@misp.local > /var/www/MISP/app/webroot/gpg.asc"
14 Configurazione “workers”
Come ultimissima cosa, configuriamo i workers di MISP per avviarsi all’avvio del sistema. I workers permettono una moteplicità di operazioni alla piattaforma, molte delle quali critiche. Consentono ad esempio la gestione dei job di sincronizzazione fra più server MISP, la gestione delle code email, della cache applicativa e molto altro. È vivamente consigliata la configurazione come da manuale di questo elemento.
Per prima cosa, diamo allo script di avvio dei workers i permessi di esecuzione.
:~$ sudo chmod +x /var/www/MISP/app/Console/worker/start.sh
Di seguito modifichiamo il file /etc/rc.local per richiamare lo script all’avvio del sistema.
:~$ sudo nano /etc/rc.local
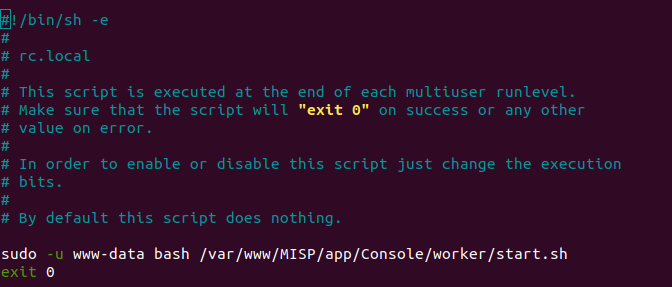
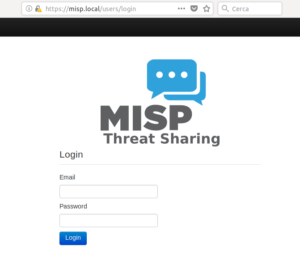
15 Riavvio e primo login
A questo punto è possibile riavviare il server e successivamente visitare la pagina web https://misp.local (sostituite la URL con il vosto FQDN scelto). E se le istruzioni sono andate a buon fine, vi troverete di fronte la form di login, in cui userete come prime e temporenee credenziali la coppia nome utente/password “admin@admin.test/admin“.
16 Hardening
È necessario procedere alla hardenizzazione di tutto quanto fin qui installato e configurato. In particolare:
- Il sistema operativo;
- Il webserver Apache;
- MariaDB;
- Altro…
17 Funzionalità opzionali
MISP utilizza ZeroMQ per alcuni importanti aspetti delle funzionalità di sottoscrizione e sharing. La funzionalità è presentata come opzionale dal team di MISP, in quanto ci sono diverse modalità di sottoscrizione e sharing utilizzando MISP. Tuttavia si consiglia vivamente di installare ed abilitare le funzionalità di ZeroMQ, al fine di non privarsi della potenza del software con piene funzionalità.
Eseguire i due comandi che seguono.
:~$ sudo pip install pyzmq :~$ sudo pip install redis
Conclusioni
Il lettore più attento avrà notato come la procedura di installazione di MISP sia tutt’altro che banale. Questo perché MISP è una vera e propria “Piattaforma”. Ovvero un set di strumenti e servizi che consentono l’archiviazione, la correlazione, l’analisi e lo sharing di informazioni riguardanti in particolare aspetti vicini alla sicurezza informatica.
Comprendere la profonda interazione che si crea dall’uso di tali strumenti, serve ad un uso consapevole dell’applicativo e delle sue potenzialità. MISP offre un contesto operativo modulare ed estendibile. In grado di adattarsi ai diversi contesti operativi.
Mi riprometto di scrivere, tempo permettendo, altri post sull’argomento. HTH.